Written with contributions from Bryon Singh, Director of Security Operations, RailWorks Corporation
The Matrix and the Power of Choosing the Right Reality
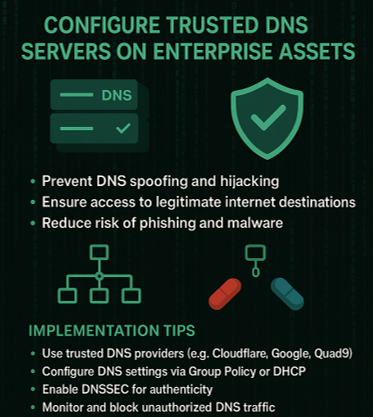
In the 1999 sci-fi classic The Matrix, Neo is offered a choice: take the red pill and see the truth, or take the blue pill and remain in a fabricated illusion. This iconic moment is more than just cinematic gold, it’s a perfect metaphor for CIS Safeguard 4.9, which urges organizations to configure trusted DNS servers on all enterprise assets.
Just like Neo’s choice determined whether he saw the real world or a manipulated one, your choice of DNS servers determines whether your systems access legitimate internet destinations or fall prey to malicious redirections.
What Is CIS Safeguard 4.9?
CIS Safeguard 4.9 is part of the Center for Internet Security (CIS) Critical Security Controls, specifically under Control 4: Secure Configuration of Enterprise Assets and Software. This safeguard recommends:
“Configure trusted DNS servers on enterprise assets to ensure DNS queries are resolved by known, secure, and monitored servers.”
Why It Matters
DNS (Domain Name System) is like the phonebook of the internet. When you type a website address, DNS translates it into an IP address so your device can connect to the correct server.
But here’s the catch: if your DNS server is compromised or untrusted, it can redirect you to malicious sites, even if you typed the correct URL. This is known as DNS spoofing or DNS hijacking.
Real-World Risks:
- Phishing attacks that look like legitimate websites
- Malware downloads from spoofed domains
- Data interception and surveillance
How to Implement Safeguard 4.9
Here’s how to take the “red pill” and secure your DNS reality:
- Use Trusted DNS Providers
Choose DNS services known for security and privacy, such as:
- Google Public DNS (8.8.8.8, 8.8.4.4)
- Cloudflare DNS (1.1.1.1)
- Quad9 (9.9.9.9)
- Configure DNS Settings on All Devices
Apply DNS settings via:
- Group Policy (for Windows environments)
- DHCP server configurations
- Endpoint management tools
- Enable DNSSEC (DNS Security Extensions)
This adds cryptographic signatures to DNS data, ensuring authenticity.
- Monitor DNS Traffic
Use DNS logging and monitoring tools to detect anomalies or unauthorized changes.
- Block Untrusted DNS Requests
Prevent devices from using rogue DNS servers by enforcing firewall rules.
Final Thoughts: Choose the Right Reality
In The Matrix, Neo’s journey begins with a simple choice. In cybersecurity, configuring trusted DNS servers is one of those deceptively simple but powerful decisions. It’s a foundational step that protects your organization from a wide range of threats.
So ask yourself: are your systems seeing the real internet—or a dangerous illusion?
Resources
Here’s a link to the Secure Configuration Management for CIS Control 4, 9, and 12 provided free of charge from the fine folks at the Center for Internet Security:
Looking for even more detail? Here you go. If this still doesn’t satisfy your curiosity, DM me.
CIS Control 4 – Secure Configuration of Enterprise Assets and Software
Develop processes and technical controls to identify, classify, securely handle, retain, and dispose of data.
CIS Safeguard 4.9: - Configure Trusted DNS Servers on Enterprise Assets
Configure trusted DNS servers on network infrastructure. Example implementations include configuring network devices to use enterprise-controlled DNS servers and/or reputable externally accessible DNS servers.