Perhaps one of the most popular features of Exchange is the ability to connect Outlook running on a PC to Exchange over the Internet when outside the corporate network without the need to establish a VPN connection. This feature was introduced with Exchange 2003 and is called Outlook Anywhere. Of course, convenience always comes at a price: once enabled, Outlook Anywhere allows anyone with Outlook to connect to Exchange from any PC regardless of who owns it. Many organizations want or need to restrict Outlook Anywhere access to corporate owned devices and hence disallow access from personal computers (BYOD). Some organizations prevent external Outlook Anywhere access altogether.
Enter cloud computing and Exchange Online (EOL). EOL allows Outlook Anywhere access by default and cannot be simply disabled on the backend, like it can be with an on-premises Exchange infrastructure. This does not mean that Outlook Anywhere cannot be controlled. What it does mean is that the methods for controlling access are different than they are for on-premises Exchange. This blog shows you how to implement one option for limiting Outlook access to the full desktop client on a PC to corporate owned devices.
The magic to this method of restricting Outlook access is through AAD Conditional Access policies. Conditional Access is based on the premise that the security needs of organizations today extend beyond the walls of the corporate network and must include user and device identity. Conditional Access policies allow an organization to control access to cloud-based apps based on conditions.
In this example, corporate owned devices are defined by PCs that are Hybrid Azure AD joined. I won’t cover how to enable Hybrid Azure Active Directory (AAD) join in this blog. Suffice it to say that Hybrid AAD join requires proper planning and needs to be enabled in ADConnect. Also, currently this policy will only work on PCs that are hybrid AAD joined and will not work for PCs that are Azure AD joined. Hopefully, Microsoft will add support for Azure AD joined machines in the future.
Conditional Access requires one of the Azure AD Premium licenses.
Conditional Access policies are configured in the Azure Admin Console:
- Login to the Azure Admin Center: https://portal.azure.com
- Click on Conditional Access. If it is not shown as an option on login, type Conditional Access in the search bar at the top center of the screen. The screen shot below shows the existing policies.
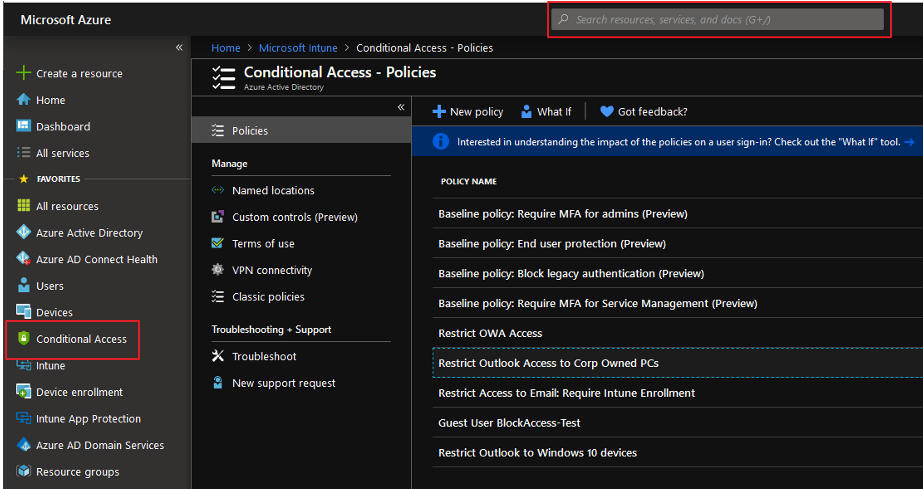
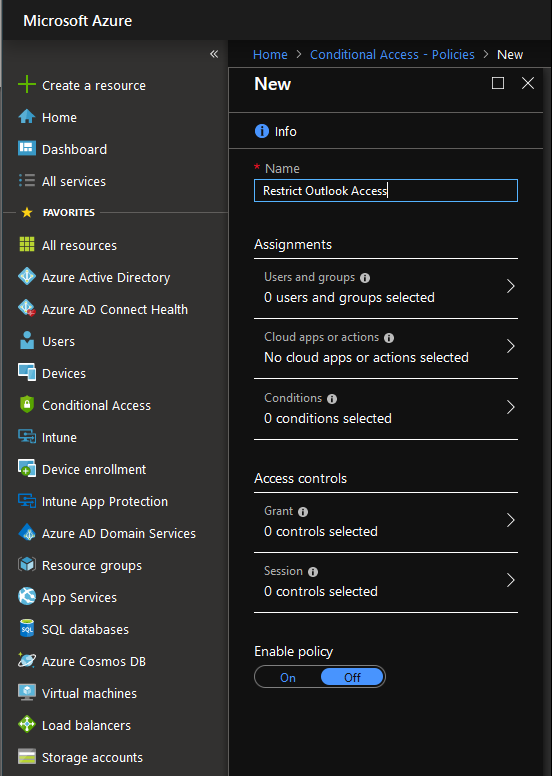
- Create a new policy: Click New policy and give it a name, such as Restrict Outlook Access. Note the policy is disabled by default. Make sure to enable it.
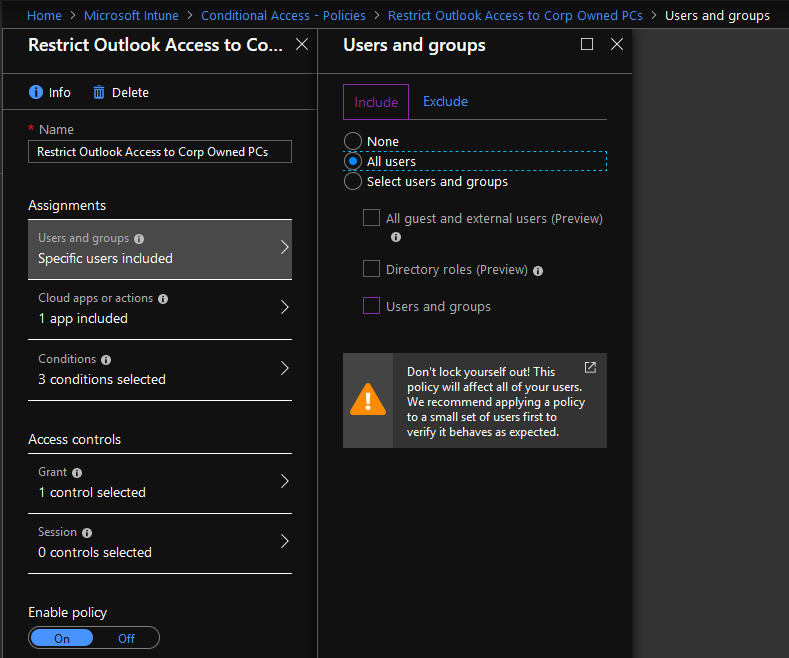
- Next, assign users. Click Users and groups under Assignments. In the Users and Groups blade, select the users you want the policy to apply to.
- Suggestion: begin by applying the policy to test / pilot users rather than selecting all users. Make sure the policy is working correctly before applying to all users, if that is the desired state. If you are not careful, you can cut off Outlook access for all users if the policy is not configured as desired.
- Click the Select users and groups radio button
- Click the Users and groups check box
- Select the users/groups to apply the policy to in the Select blade. When the users/groups have been selected, click the Select button and then the Done button on the Users and groups blade.
- Select the Apps to apply the policy to: Click Cloud apps or actions
- Click the Select apps radio button in the Cloud apps or actions blade and then click Select.
- A new blade will appear with a list of applications to apply to the policy. Select Office 365 Exchange Online. Click the Select button at the bottom of the blade.
- Click the Done button at the bottom of the Cloud apps or action blade.
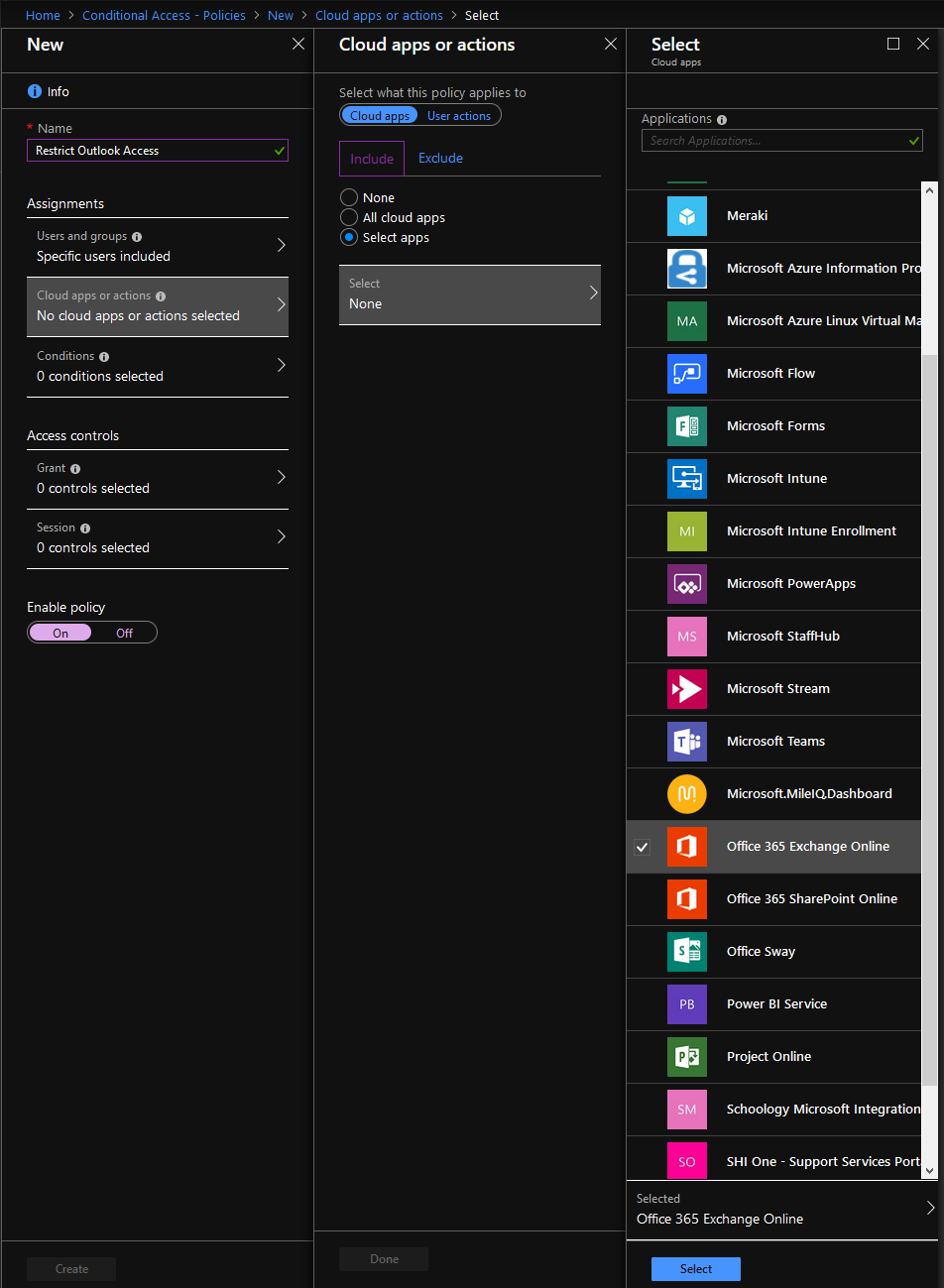
- Now, let’s apply the conditions for the policy: Select Conditions, this will present the Conditions blade.
- Select Device platforms. On the Device Platforms blade:
- Click the Yes button on the Configure slider
- Click the Include tab
- Click the Select device platforms radio button
- Click the Windows check box
- Click the Done button to close the Device platforms blade
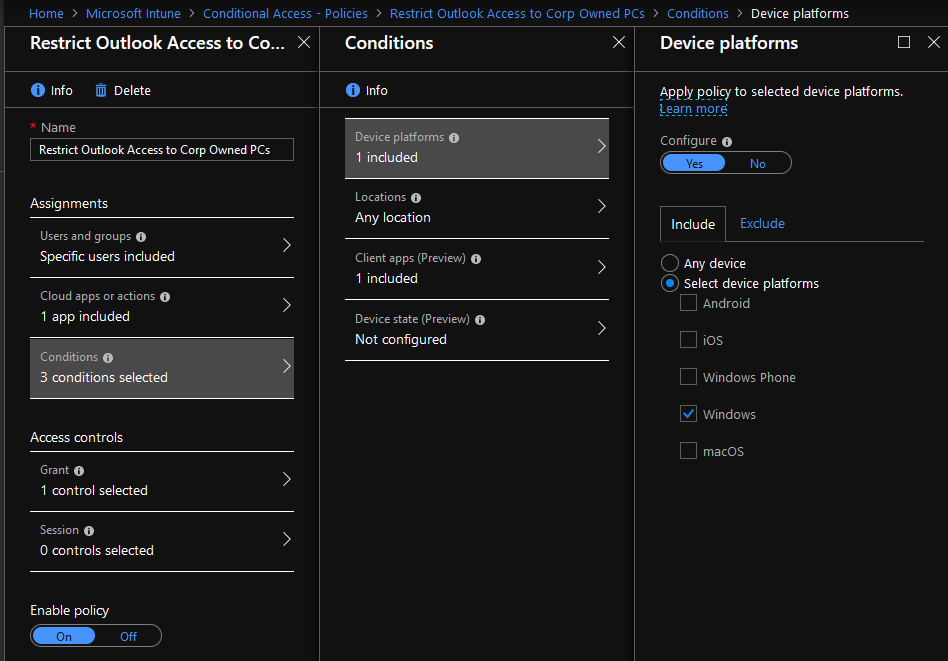
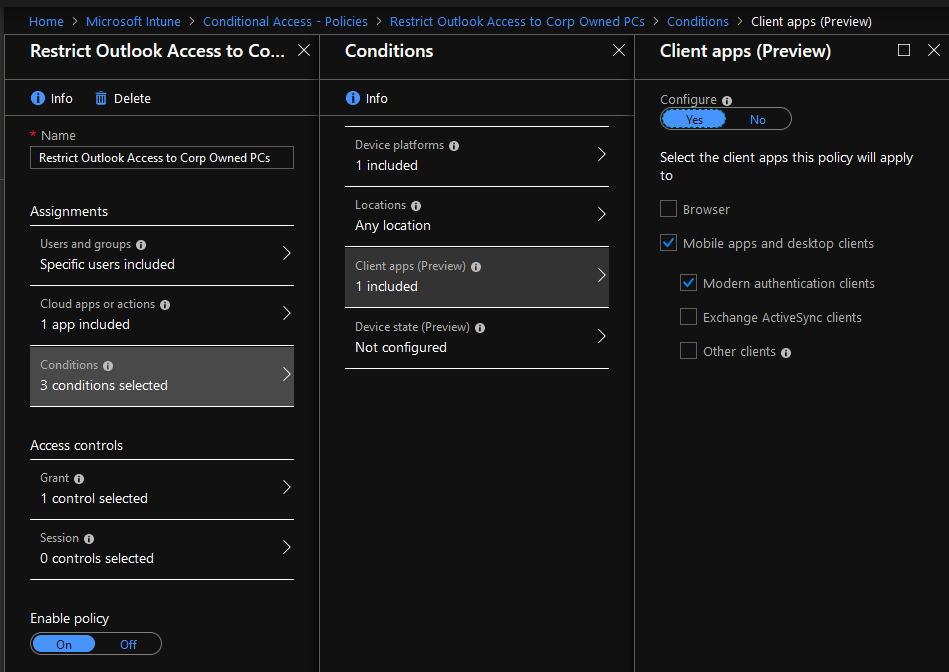
- Click on Client apps on the Conditions blade, which opens a new blade
- Click the Yes button on the Configure slider
- Click Modern apps and desktop clients
- Click Modern authentication clients
- Make sure no other options are selected
- Click the Done button on the Client apps blade
- Click the Done button on the Conditions blade
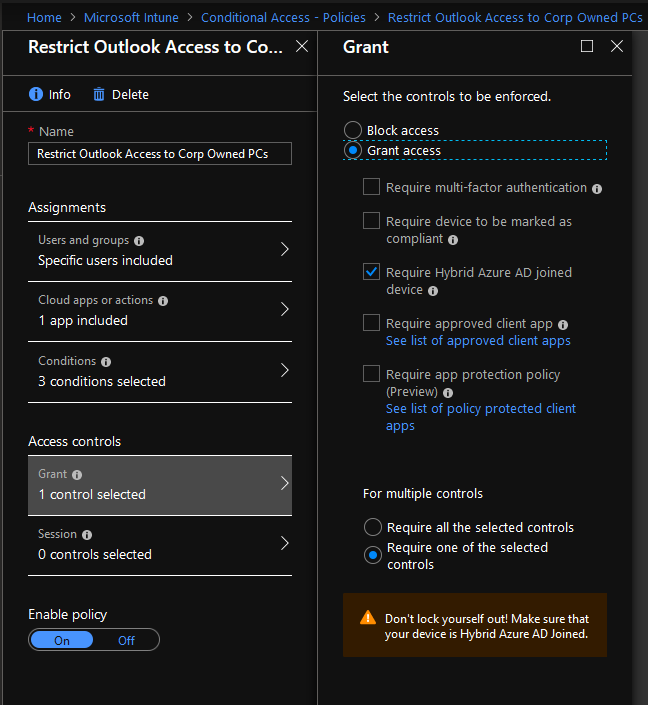
- Select Grant (under Access Controls), which presents the Grant blade
- Click Grant Access
- Click the Require Hybrid Azure AD joined device check box
- Click the Require one of the selected controls radio button
- Click the Select button to close the Grant blade
- To complete the policy click the Create button
Be careful with this setting. Once selected, any machine that needs Outlook access must be hybrid joined. As such, make sure PCs that require Outlook access have been hybrid joined. You can limit the scope of the policy by assigning it to specific users/groups as described above.
If you are ready to test the policy, make sure to enable it by selecting On under the Enable policy slider. Remember that this policy requires PCs to be Hybrid Azure AD joined. All other PCs will be denied access.
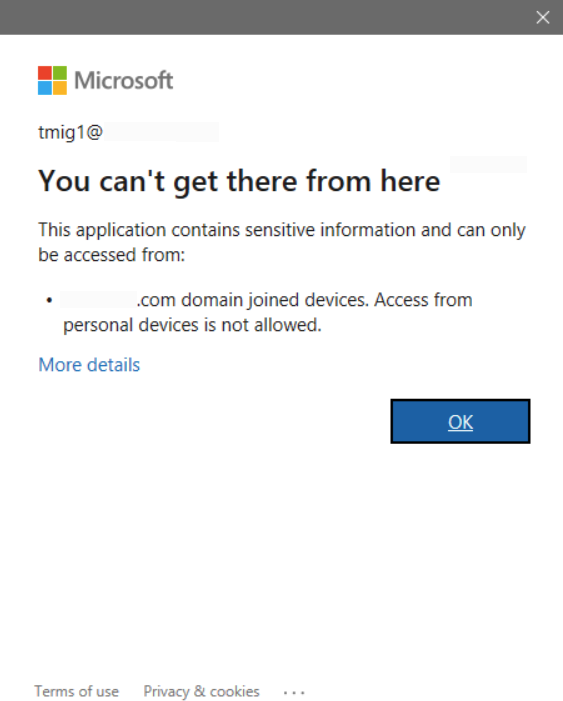
Once the Conditional Access policy is configured and enabled, it will prevent users from connecting to Exchange Online. When a user attempts to create an Outlook profile to connect to EOL, the user will be denied access when configuring the profile. If a profile has already been created (before the policy was put in place), the user will also be denied access. In both cases, after a user is prompted for credentials to connect to EOL, the following message will be displayed.